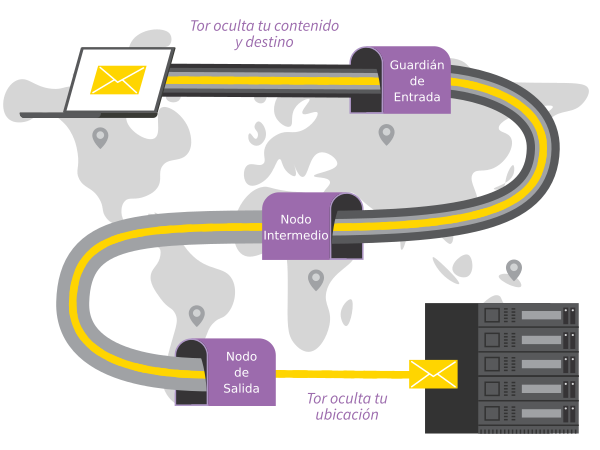
Todo lo que haces en Internet desde Tails pasa por la red Tor.
Tor cifra y anonimiza tu conexión pasándola a través de 3 repetidores. Los repetidores de Tor son servidores operados por diferentes personas y organizaciones en todo el mundo.
No puedes acceder a Internet desde Tails hasta que estés conectado a
Tor. Por ejemplo, el Navegador Tor muestra el mensaje de error El
servidor proxy rechaza conexiones hasta que esté conectado a Tor.
Como Tor enruta tu tráfico de Internet a través de 3 repetidores antes de llegar a su destino, la conexión es más lenta que cuando no estás usando Tor.
Consulta nuestra documentación sobre por qué Tor es lento.
Para conectarse a la red Tor:
Conéctate a una red local, cableada, Wi-Fi, o móvil.
El asistente Tor Connection aparece para ayudarte a conectarte a la red Tor.
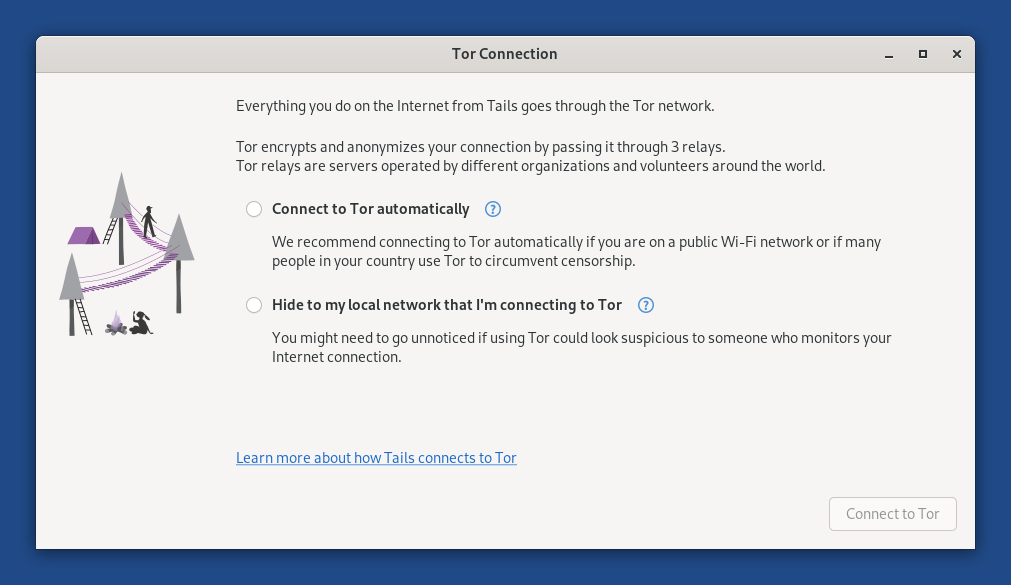
Elige si deseas:
Conectar a Tor automáticamente
Ocultar a la red local que estás usando Tor
Las implicaciones de ambos métodos se detallan a continuación.
Repetidores Tor y puentes
Public Tor relays
La mayoría de las veces, tu red local no bloquea el acceso a la red Tor y puedes usar un repetidor público como tu primer repetidor Tor.
Using a public Tor relay as your first Tor relay makes it clear to your local network that you are connecting to Tor, while still keeping your online activity secure and anonymous.
Tor bridges
Los puentes de Tor son repetidores de Tor secretos que mantienen tu conexión con la red Tor oculta.
Utiliza un puente como tu primer repetidor de Tor si la conexión a Tor está bloqueada o si usar Tor podría parecer sospechoso para alguien que monitorea tu conexión a Internet.
La tecnología utilizada por los puentes de Tor está diseñada para evitar la censura donde las conexiones a Tor están bloqueadas, por ejemplo en algunos países con fuerte censura, por algunas redes públicas, o por algunos controles parentales.
Lo hace camuflando tu conexión para que no pueda ser reconocida como una conexión a Tor. Como consecuencia, se puede utilizar la misma tecnología para ocultar que estás usando Tor si pudiese parecer sospechoso para alguien que monitorea tu conexión a Internet.
Los puentes de Tor suelen ser menos fiables y más lentos que los repetidores de Tor públicos.
Conectarse a Tor automáticamente
Recomendamos conectarse a Tor automáticamente si está en una red Wi-Fi pública o si muchas personas en su país usan Tor para eludir la censura.
Cuando eliges esta opción:
Primero, Tails sincroniza el reloj del ordenador automáticamente, porque se necesita una hora correcta para poder conectarse a la red Tor.
Tails aprende la hora actual conectándose al servicio de detección del portal cautivo de Fedora, que es utilizado por la mayoría de las distribuciones de Linux. Esta conexión no va a través de la red Tor y es una excepción a nuestra política de sólo hacer conexiones a Internet a través de la red Tor.
You can learn more about our security assessment of this time synchronization in our design documentation about non-Tor traffic.
Si en su lugar eliges ocultar que te estás conectando a Tor, puede que tengas que arreglar el reloj del ordenador manualmente.
If Tails fails to synchronize the clock because you have to sign in to the network using a captive portal, an error screen is displayed that helps you do so.
For detailed instructions, see how to sign in to the network using a captive portal.
Then, Tails tries different ways of connecting to Tor until it succeeds:
Tails tries to connect to Tor directly using public relays, without using a bridge.
Tails tries to connect to Tor using one of the default bridges, already included in Tails, if connecting using public relays fails.
Tails uses the default obfs4 bridges from Tor Browser.
If public relays and default bridges don't work, Tails asks you to configure a custom bridge, if connecting using the default bridges fails.
Alguien que esté monitoreando tu conexión a Internet podría identificar estos intentos como provenientes de un usuario de Tails.
Ocultar a la red local que estás usando Tor
You might need to go unnoticed if using Tor could look suspicious to someone who monitors your Internet connection.
Cuando eliges esta opción, Tails solo se conectará a Tor después de configurar un puente de Tor personalizado. Los puentes son repetidores de Tor secretos que ocultan que te estás conectando a Tor.
It is impossible to hide to the websites that you visit that you are using Tor, because the list of exit nodes of the Tor network is public.
Our team is doing its best to help you connect to Tor using the most discreet types of Tor bridges. That is why, when you decide to hide that you are connecting to Tor:
Tails does not automatically detect whether you have to sign in to the network using a captive portal.
Default bridges are not available.
To learn about other Tor bridges, you have several options listed below.
You can use obfs4 and WebTunnel bridges in Tails right now.
None of these options is easy to do from Tails, so we recommend that you learn about several bridges from your regular computer before starting Tails and store the bridge lines in a text document on separate USB stick.
After you restarted on Tails, you can copy one of these bridge lines from this other USB stick into Tor Connection.
Even someone who knows your bridge cannot know what you are doing online from Tails.
Website
You can visit https://bridges.torproject.org/options.
We recommend doing so from a different local network if you want to hide that you are connecting to Tor.
Correo electrónico
You can send an empty email to bridges@torproject.org from a Gmail or Riseup email address.
Sending the email reveals to Gmail or Riseup that you are trying to connect to Tor but not to someone who monitors your Internet connection.
Telegram
You can send the message
/bridgesto @GetBridgesBot on Telegram.
To save the last Tor bridge that connected to Tor successfully, turn on the Tor Bridge feature of the Persistent Storage.
In the future, we will make it easier to use a custom bridge by:
Troubleshooting connecting to Tor
See our documentation on troubleshooting connecting to Tor.
Viewing the status of Tor
The status of Tor appears as an onion icon in the notification area:
 You are connected to Tor.
You are connected to Tor. You are not connected to Tor.
You are not connected to Tor.
To view the list of Tor circuits that are used by your different applications, click on the Tor status icon and choose View Tor Circuits. Learn more about managing Tor circuits.
