Notizie
Subscribe to our newsletter to receive the same news by email:
Changes and updates
Fixed problems
For more details, read our changelog.
Get Tails 6.19
To upgrade your Tails USB stick and keep your Persistent Storage
Automatic upgrades are available from Tails 6.0 or later to 6.19.
If you cannot do an automatic upgrade or if Tails fails to start after an automatic upgrade, please try to do a manual upgrade.
To install Tails 6.19 on a new USB stick
Follow our installation instructions:
The Persistent Storage on the USB stick will be lost if you install instead of upgrading.
To download only
If you don't need installation or upgrade instructions, you can download Tails 6.19 directly:
Tails 7.0~rc2 is the second release candidate of the upcoming Tails 7.0.
We plan to release Tails 7.0 officially on September 18 or on October 16. You can help us by testing this release candidate already.
Tails 7.0 will be the first version of Tails based on Debian 13 (Trixie) and GNOME 48. It will bring new versions of many applications included in Tails.
We have tested 7.0~rc2 with the same extensive automatic and manual test suites that we use for regular releases. But, Tails 7.0~rc2 might still contain undiscovered issues.
We will provide automatic security upgrades for Tails 7.0~rc2, like we do for regular versions.
Changes and updates
Changes since 7.0~rc1
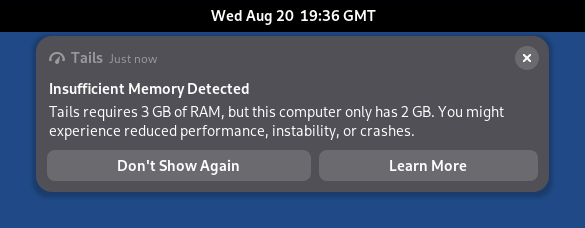
Increase the memory requirements from 2 GB of RAM to 3 GB. (#21114)
Tails 7.0~rc2 displays a notification when the RAM requirements are not met.
We estimate that less than 2% of current users will be affected.
Remove the Places menu. (#21086)
Rename Root Terminal as Root Console. (#21110)
Skip the onboarding of Inkscape. (#21091)
Other changes compared with 6.18
Replace GNOME Terminal with GNOME Console. (#20161)
Replace GNOME Image Viewer with GNOME Loupe (#20640)
Remove Kleopatra from the Favorites menu. (#21072)
To start Kleopatra choose Apps ▸ Accessories ▸ Kleopatra.
Remove the obsolete Network Connection option from the Welcome Screen. (#21074)
Included software
Update the Tor client to 0.4.8.17.
Update Thunderbird to 128.13.0esr.
Update the Linux kernel to 6.12.41.
This improves support for newer hardware: graphics, Wi-Fi, and so on.
Update Electrum from 4.3.4 to 4.5.8.
Update OnionShare from 2.6.2 to 2.6.3.
Update KeePassXC from 2.7.4 to 2.7.10.
Update Kleopatra from 4:22.12 to 4:24.12
Update Inkscape from 1.2.2 to 1.4.
Update GIMP from 2.10.34 to 3.0.4.
Update Audacity from 3.2.4 to 3.7.3.
Update Text Editor from 43.2 to 48.3.
Update Document Scanner from 42.5 to 46.0.
Removed software
Fixed problems
- Fix selecting the correct keyboard for certain languages. (#12638)
For more details, see the list of closed issues on the 7.0 milestone in GitLab.
Known issues
Tails 7.0~rc2 takes longer to start.
We plan to fix this in the final Tails 7.0.
For more details, see the list of issues on the 7.0 milestone in GitLab.
Send your feedback
Please, report any new problem to either:
tails-testers@boum.org (public mailing list)
support@tails.net (private email)
Get Tails 7.0~rc2
Direct download
BitTorrent download
To upgrade your Tails USB stick and keep your Persistent Storage
You can do a manual upgrade to Tails 7.0~rc2.
Automatic upgrades are not available to Tails 7.0~rc2.
To install Tails 7.0~rc2 on a new USB stick
Follow our installation instructions:
The Persistent Storage on the USB stick will be lost if you install instead of upgrading.
We are very excited to present you with a release candidate of the upcoming Tails 7.0.
We plan to release Tails 7.0 officially on October 16. You can help us by testing this release candidate already.
Tails 7.0 will be the first version of Tails based on Debian 13 (Trixie) and GNOME 48. It will bring new versions of many applications included in Tails.
We have tested 7.0~rc1 with the same extensive automatic and manual test suites that we use for regular releases. But, Tails 7.0~rc1 might still contain undiscovered issues.
We will provide automatic security upgrades for Tails 7.0~rc1, like we do for regular versions.
Changes and updates
Replace GNOME Terminal with GNOME Console. (#20161)
We broke the Root Terminal while working on this change.
To open a root terminal, execute the following command in a regular Console.
sudo -i
Replace GNOME Image Viewer with GNOME Loupe (#20640)
Remove Kleopatra from the Favorites menu. (#21072)
To start Kleopatra choose Apps ▸ Accessories ▸ Kleopatra.
Remove the obsolete Network Connection option from the Welcome Screen. (#21074)
Included software
Update the Tor client to 0.4.8.17.
Update Thunderbird to 128.13.0esr.
Update the Linux kernel to 6.12.38.
This improves support for newer hardware: graphics, Wi-Fi, and so on.
Update Electrum from 4.3.4 to 4.5.8.
Update OnionShare from 2.6.2 to 2.6.3.
Update KeePassXC from 2.7.4 to 2.7.10.
Update Kleopatra from 4:22.12 to 4:24.12
Update Inkscape from 1.2.2 to 1.4.
Update GIMP from 2.10.34 to 3.0.4.
Update Audacity from 3.2.4 to 3.7.3.
Update Text Editor from 43.2 to 48.3.
Update Document Scanner from 42.5 to 46.0.
Removed software
Fixed problems
- Fix selecting the correct keyboard for certain languages. (#12638)
For more details, see the list of closed issues on the 7.0 milestone in GitLab.
Known issues
Tails 7.0~rc1 requires 3 GB of RAM instead of 2 GB to run smoothly. (#18040)
We estimated that less than 2% of current users will be affected.
Tails 7.0~rc1 takes longer to start.
We plan to fix this in the final Tails 7.0.
For more details, see the list of issues on the 7.0 milestone in GitLab.
Send your feedback
Please, report any new problem to either:
tails-testers@boum.org (public mailing list)
support@tails.net (private email)
Get Tails 7.0~rc1
Direct download
-
OpenPGP signature
For DVDs and virtual machines (ISO image)
OpenPGP signature
BitTorrent download
For USB sticks (USB image)
For DVDs and virtual machines (ISO image)
To upgrade your Tails USB stick and keep your Persistent Storage
You can do a manual upgrade to Tails 7.0~rc1.
Automatic upgrades are not available to Tails 7.0~rc1.
To install Tails 7.0~rc1 on a new USB stick
Follow our installation instructions:
The Persistent Storage on the USB stick will be lost if you install instead of upgrading.
New features
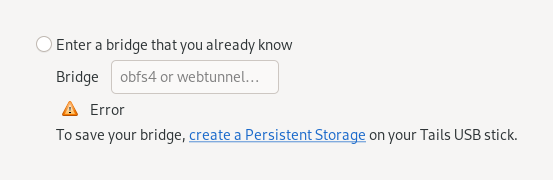
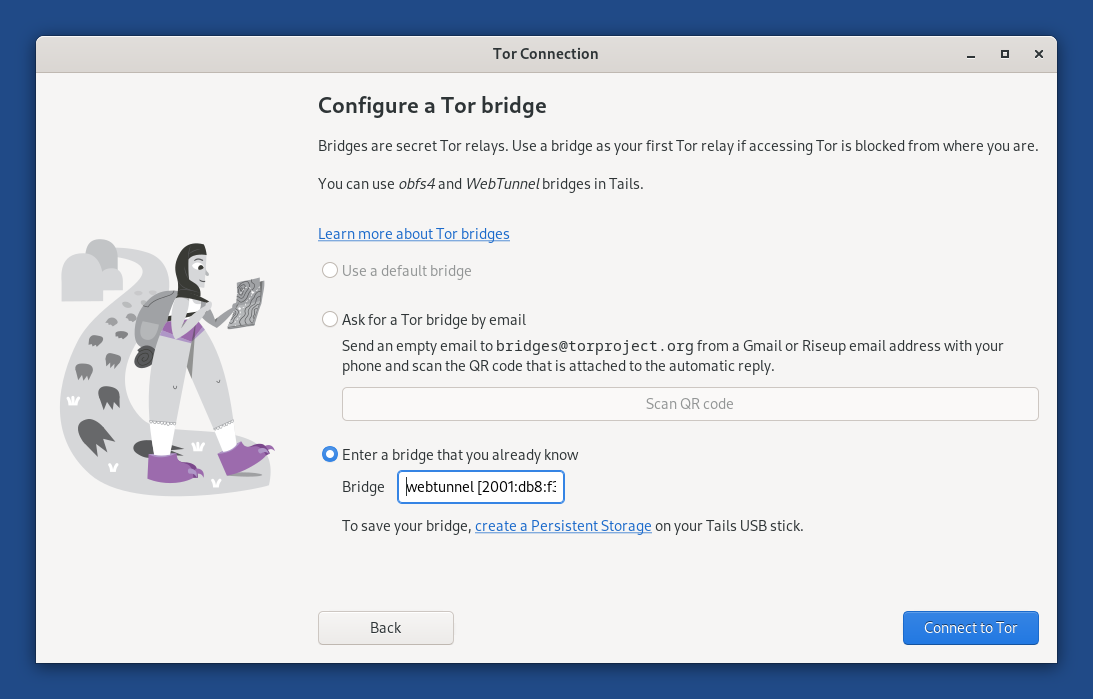
WebTunnel bridges
You can now use WebTunnel bridges to connect to the Tor network from Tails.
WebTunnel is a bridge technology that is particularly good at circumventing censorship and might work from places where obfs4 bridges are blocked. WebTunnel disguises your connection as ordinary web traffic.
To get WebTunnel bridges, visit https://bridges.torproject.org/.
Changes and updates
For more details, read our changelog.
Get Tails 6.18
To upgrade your Tails USB stick and keep your Persistent Storage
Automatic upgrades are available from Tails 6.0 or later to 6.18.
If you cannot do an automatic upgrade or if Tails fails to start after an automatic upgrade, please try to do a manual upgrade.
To install Tails 6.18 on a new USB stick
Follow our installation instructions:
The Persistent Storage on the USB stick will be lost if you install instead of upgrading.
To download only
If you don't need installation or upgrade instructions, you can download Tails 6.18 directly:
Changes and updates
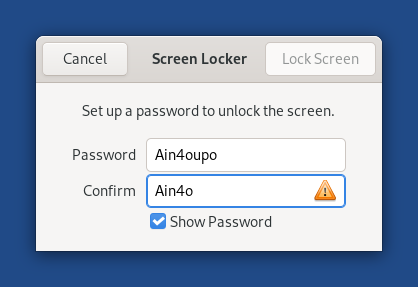
Add a Show Password option when setting the screen locking password.
Update the uBlock Origin extension for Tor Browser to 1.62.0.
Update Tor Browser to 14.5.4.
Fixed problems
Display an empty page instead of the homepage of Tor Browser when opening new tabs in the Unsafe Browser. (#21004)
Remove duplicated CPU microcode to reduce image size. (#21001)
For more details, read our changelog.
Get Tails 6.17
To upgrade your Tails USB stick and keep your Persistent Storage
Automatic upgrades are available from Tails 6.0 or later to 6.17.
If you cannot do an automatic upgrade or if Tails fails to start after an automatic upgrade, please try to do a manual upgrade.
To install Tails 6.17 on a new USB stick
Follow our installation instructions:
The Persistent Storage on the USB stick will be lost if you install instead of upgrading.
To download only
If you don't need installation or upgrade instructions, you can download Tails 6.17 directly:
Changes and updates
Update Tor Browser to 14.5.3.
Update the Linux kernel to 6.1.140.
For more details, read our changelog.
Get Tails 6.16
To upgrade your Tails USB stick and keep your Persistent Storage
Automatic upgrades are available from Tails 6.0 or later to 6.16.
If you cannot do an automatic upgrade or if Tails fails to start after an automatic upgrade, please try to do a manual upgrade.
To install Tails 6.16 on a new USB stick
Follow our installation instructions:
The Persistent Storage on the USB stick will be lost if you install instead of upgrading.
To download only
If you don't need installation or upgrade instructions, you can download Tails 6.16 directly:
Nine months ago Tails and Tor set out to unite forces for Internet Freedom. The goal was to integrate Tails into the organizational structure of the Tor Project to pool resources instead of duplicating them, and deliver a more robust shield against censorship and surveillance. Today we're happy to report that we're already seeing the transformative impact of our united efforts.
Delivering on our promises
The integration of two organizations requires careful planning and collaboration. When we first began our discussions, we made it a point to focus on better serving the shared communities that depend on Tor and Tails. The merger has already delivered on our core commitments in concrete ways:
Countering censorship and surveillance more effectively
Our combined anti-censorship expertise is yielding immediate results. Whenever a new or previously unknown censorship event occurs, we can figure out how best to tackle the issues. China is one such example in action: When obfs4 bridges increasingly became the target of censors, our teams were able to jointly coordinate a strategic response, determining whether to address the issue through improved bridge distribution mechanisms or by adding support for newer pluggable transports in Tails itself. This kind of coordinated response to censorship events was more challenging and time-consuming when we operated separately.
More robust treatment of overlapping threat models
We've ensured that Tails' specific needs are now directly integrated into Arti development, creating a more comprehensive solution for users who need both network and system-level security in high-risk environments. Having both Tor Browser and Tails developers collaborate more closely means that Tails users benefit from smoother, earlier releases that provide user protections faster.
Expanded training and outreach opportunities
Empowering our users through access and digital rights education has been a top priority for both Tails and Tor. Earlier this year, we successfully ran a Tails training in partnership with the Open Culture Foundation the day before RightsCon 2025, reaching activists and journalists who urgently need these tools. By tapping into Tor's Privacy Resilience Grants, we're now supporting more groups in the Global South to run Tails trainings directly in their communities, expanding Tails' reach to new territories and user groups.
Operational resilience to advance our shared mission
The benefits extend far beyond individual projects. Our unified sysadmin team has created a comprehensive 5-year roadmap for merging our digital infrastructures, eliminating redundancies while strengthening both organizations' technological foundations. We've already merged critical services including calendars, GitLab projects, password stores, and documentation systems, with security policies, monitoring systems, and authentication mechanisms currently in progress.
The merger has also clarified roles and responsibilities across teams while providing Tails teams with access to the Tor Project's mature organizational structure and improving system monitoring and management. Our expanded fundraising capacity means we can pursue larger grants and coordinate funding requests that support both tools simultaneously. It allows us to stay resilient in a dynamic fundraising landscape, and maximize the impact of every dollar.
This is a meaningful achievement for every supporter: Your donations now go further toward creating real-world impact rather than duplicating administrative overhead. Our resources are now fully directed toward developing stronger privacy tools and reaching more people who need protection from surveillance and censorship.
Upcoming changes for PayPal donors
Tails, just like Tor, has always been powered by your donations. As part of our organizational merge, we are taking the opportunity to upgrade the way we manage donations, donor records, and communication with you about your donations.
If you have made a donation to Tails through PayPal, your information will be imported into Tor's CiviCRM Customer Relationship Management (CRM) database, which collects only the minimal amount of information and hosts all donor data on Tor infrastructure. Rest assured that Tor will never sell or share your data. Ever. You can read the Tor Project's privacy policy here.
The following information will be imported:
- Name
- Address, if given
- Past donation history
All of this data will be merged by June 30, 2025. Once the data is completely merged, all PayPal monthly donations will be terminated. If you have an active monthly donation to Tails through PayPal, please watch out for a message from us about migrating your donation.
What you can do today
Thank you for being defenders of online privacy, anonymity, and censorship circumvention tools. We invite all our supporters to join us as part of the unified Tor community, working together to safeguard the digital human rights of individuals worldwide. Please consider renewing your donation today for the Tor Project and help make privacy possible.
The Tor Project is a 501(c)(3) nonprofit committed to transparency. The Tor Project has a Four-Star Charity rating from Charity Navigator, and has been awarded Candid's Platinum Seal of Transparency. This demonstrates the Tor Project's commitment to openness and honesty in how the organization manages its finances and uses your investment for a greater impact. Your donation is in good hands and goes a long way.
This release is an emergency release to fix important security vulnerabilities in Tor Browser.
Changes and updates
Update Tor Browser to 14.5.2, which fixes Mozilla Foundation Security Advisory 2025-37. These vulnerabilities allow an attacker to perform an out-of-bounds read or write on a JavaScript object, but don't allow breaking out of the Firefox sandbox.
Update Thunderbird to 128.10.1.
Remove the Tor Browser and Tor Browser (persistent) folders: they are not necessary anymore, thanks to the more flexible confinement of Tor Browser we introduced in Tails 6.14.1. (#15028)
Fixed problems
Fix the Unsafe Browser appearing in the window list with the Tor Browser icon. (#20934)
Make reporting an error using WhisperBack more robust. (#20921)
Fix USB tethering. (#20940)
For more details, read our changelog.
Get Tails 6.15.1
To upgrade your Tails USB stick and keep your Persistent Storage
Automatic upgrades are available from Tails 6.0 or later to 6.15.1.
If you cannot do an automatic upgrade or if Tails fails to start after an automatic upgrade, please try to do a manual upgrade.
To install Tails 6.15.1 on a new USB stick
Follow our installation instructions:
The Persistent Storage on the USB stick will be lost if you install instead of upgrading.
To download only
If you don't need installation or upgrade instructions, you can download Tails 6.15.1 directly:
Late 2024, Radically Open Security conducted another security audit of critical parts of Tails.
To better protect our users, we addressed the security vulnerabilities as soon as they were discovered and reported to us, without waiting for the audit to be complete and public.
We can now share with you the final report.
The auditors concluded that:
The Tails operating system leaves a strong security impression, addressing most anonymity-related concerns. We did not find any remote code execution vulnerabilities, and all identified issues required a compromised low-privileged
amnesiauser – the default user in Tails.Looking back at the previous audit, we can see the Tails developers have made significant progress, demonstrating expertise and a serious commitment to security.
Findings
The auditors did not identify any vulnerability in:
The creation of the Persistent Storage with LUKS2, introduced in Tails 5.14 (June 2023)
Our security improvements to Thunderbird
The random seed feature, introduced in Tails 6.4 (June 2024)
The auditors found 4 issues in:
The automatic upgrade mechanism
Other important changes since Tails 5.8 (November 2023)
| ID | Impact | Description | Issue | Status | Release |
|---|---|---|---|---|---|
| OTF-001 | High | Local privilege escalation in Tails Upgrader | #20701 | Fixed | 6.11 |
| OTF-002 | High | Arbitrary code execution in Python scripts | #20702 | Fixed | 6.11 |
| #20744 | Fixed | 6.12 | |||
| OTF-003 | Moderate | Argument injection in privileged GNOME scripts | #20709 | Fixed | 6.11 |
| #20710 | Fixed | 6.11 | |||
| OTF-004 | Low | Untrusted search path in Tor Browser launcher | #20733 | Fixed | 6.12 |
Postmortem
Our team went further than simply fixing these issues. We conducted a postmortem to understand how we introduced these vulnerabilities in our releases and what we could do to avoid similar vulnerabilities in the future. This analysis led to technical, policy, and culture changes.
This analysis was useful and we'll definitely consider doing postmortems again after future audits. It might also be useful for other projects to understand how we worked on these long-lasting improvements.
Technical improvements
Postmortem of OTF-001
While preparing a major Tails release based on a new version of Debian, for example, Tails 7.0, we will look for Perl code included in Tails that modifies
@INCin a dangerous way. (#19627)Furthermore, we now automatically check for potentially vulnerable Mite code and fail the build if we find any.
Postmortem of OTF-002 (#20719 and !1911)
Our CI now ensures that all our custom Python software runs in isolated mode.
Postmortem of OTF-003 (#20711 and !1979)
Our
sudoconfiguration is now generated from a higher-level description, which has safer defaults and demands explanations when diverging from them.Postmortem of OTF-004 (#20817 and !2040)
Our CI now ensures that we don't write software that does unsafe
.desktopfile lookup.We will also periodically audit the configuration of
onion-grater, our firewall for the Tor control port. (#20821)
Policy and culture improvements
During the audit, we noticed that we lacked a policy about when we should make confidential security issues public.
This was problematic because:
We have sometimes been too secretive.
As a temporary measure, this protected our users by erring on the safe side. But, without a disclosure process, we were not meeting our own standards for transparency and openness to third-party reviews.
Different team members were working with different assumptions, which caused communication issues.
To have better guidelines for confidentiality and disclosure, we created our security issue response policy, based on the policy of the Tor Project's Network Team.
We will be more intentional about when it's worth the effort and risk to do large code refactoring.
While refactoring is necessary for a healthy software development process, this postmortem showed that large refactoring can also introduce security vulnerabilities.
When changing security-sensitive code, such as our
sudoconfiguration or any code that elevates privileges, we now require an extra review focused on security.We will communicate about security issues more broadly within our team when we discover them so that every team member can learn along the way.

Robin is an activist in struggle against a nuclear project in France. He has been using Tails as his default operating system for all his activism since 5 years, creating a clear separation between his activism (using Tails) and personal life (using encrypted Debian).
At his place, many nomadic activists use Tails USB sticks instead of having personal computers, allowing them to maintain privacy while using shared devices.
After facing repression, encrypting all their data became a baseline practice in his group. He prefers training others on Tails because it's easier to implement than teaching full computer encryption.
Because Tails is easy to share, even people with low technical abilities are able to use it. For the security of a group, what matters is the lowest security level within that group.